Which of the Following Is Considered a Secure Protocol? The Answer Revealed! Solved question which protocol was initially introduced with
If you are searching about Solved Secure VPNs use security protocols and encrypt | Chegg.com you've came to the right web. We have 25 Pictures about Solved Secure VPNs use security protocols and encrypt | Chegg.com like Understanding Secure Protocols for Data Encryption | Course Hero, What is Secure Socket Tunneling Protocol (SSTP)? and also Solved Which of the following are secure practices when | Chegg.com. Here you go:
Solved Secure VPNs Use Security Protocols And Encrypt | Chegg.com
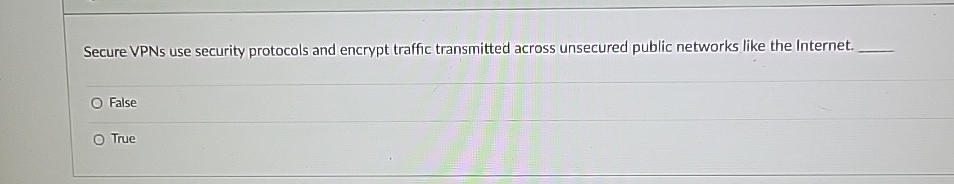 www.chegg.com
www.chegg.com
Solved Consider The Following Authentication Protocol: (1) | Chegg.com
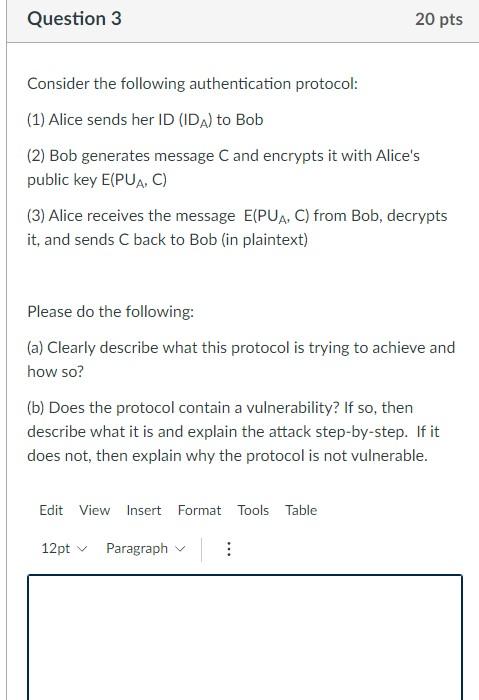 www.chegg.com
www.chegg.com
Solved Which Of The Following Are Secure Practices When | Chegg.com
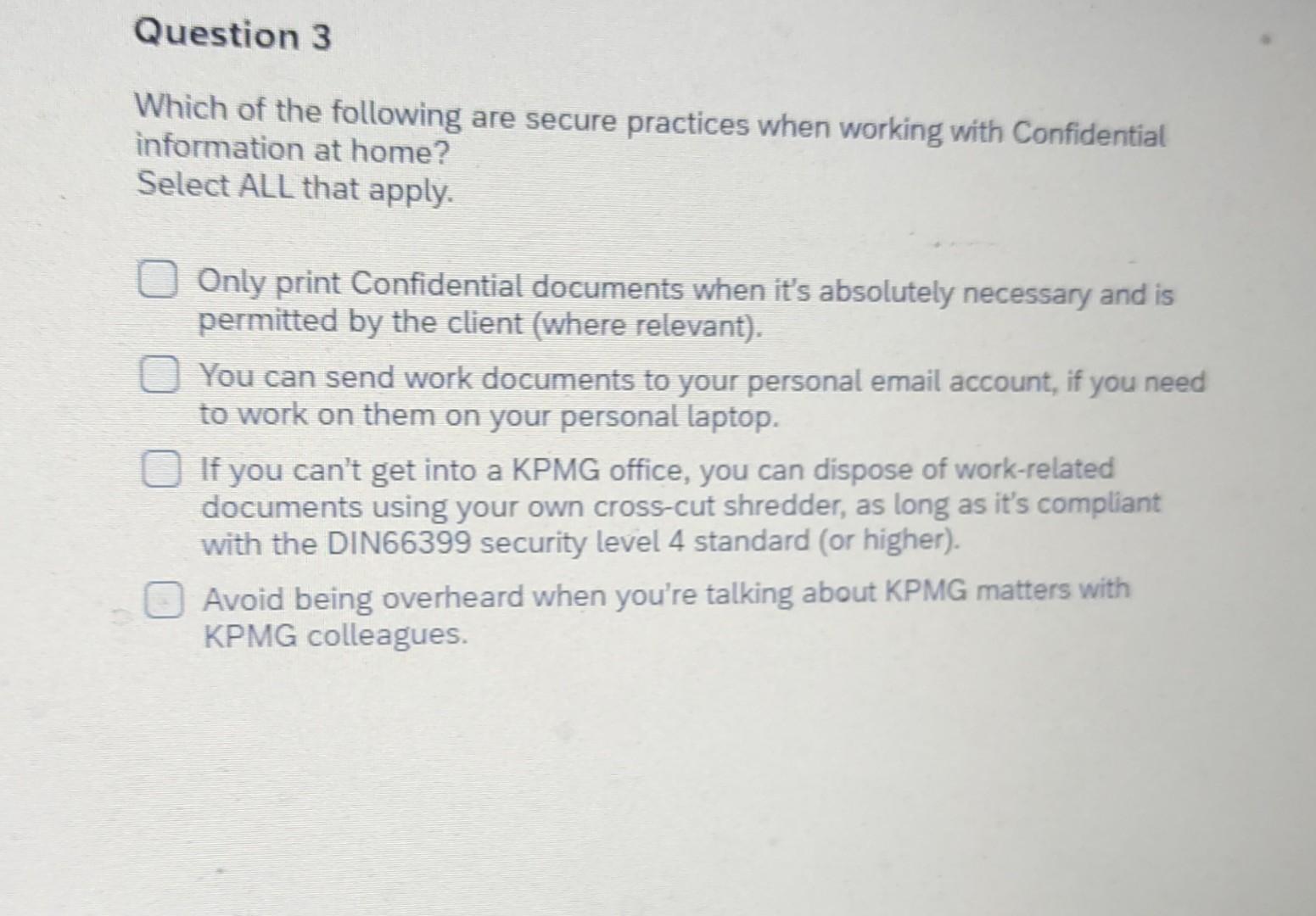 www.chegg.com
www.chegg.com
15. Network Attacks And Secure Protocols Flashcards | Quizlet
 quizlet.com
quizlet.com
Solved Consider The Following Authentication Protocol: (1) | Chegg.com
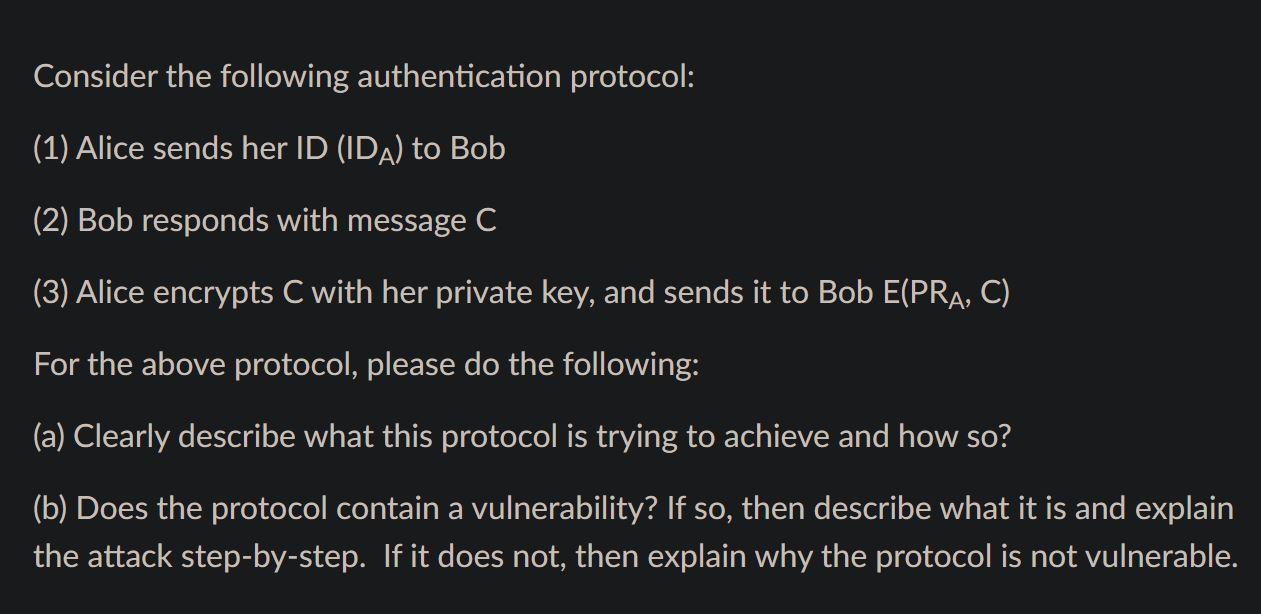 www.chegg.com
www.chegg.com
10.1.1 Secure Protocols - Secure Protocols Let's Spend A Few Minutes
 www.studocu.com
www.studocu.com
Solved Question Which Protocol Was Initially Introduced With | Chegg.com
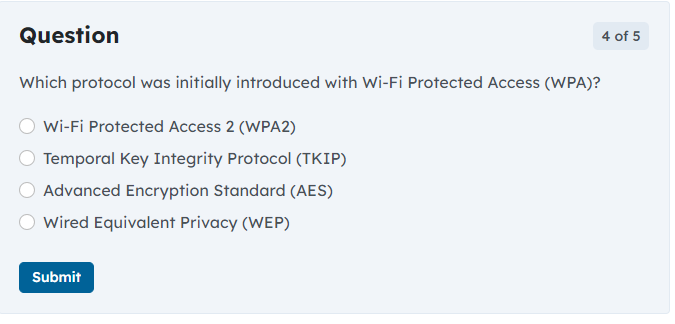 www.chegg.com
www.chegg.com
Solved Which Of The Following Protocols Can Be Secured By | Chegg.com
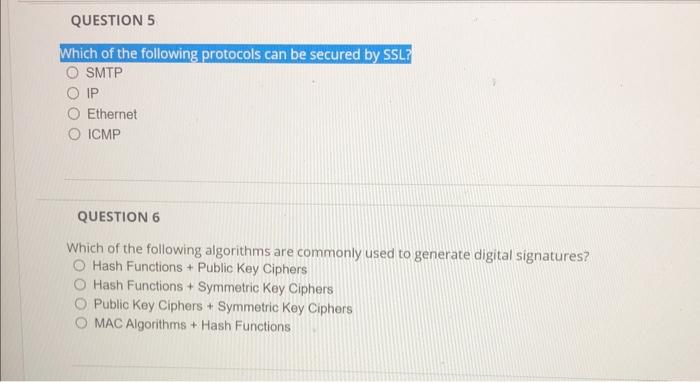 www.chegg.com
www.chegg.com
Solved Question 46 Of 100 Which Of The Following Encryption | Chegg.com
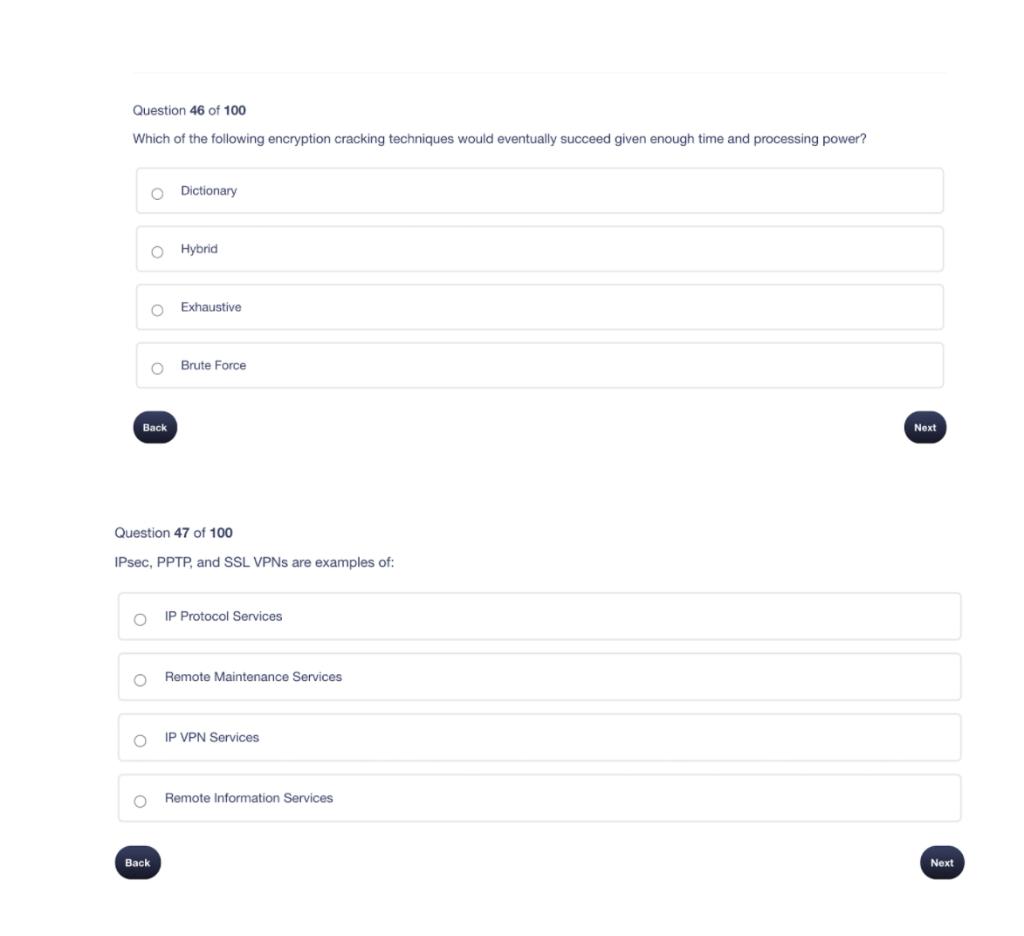 www.chegg.com
www.chegg.com
Solved Which Of The Following Techniques Can NOT Be Used To | Chegg.com
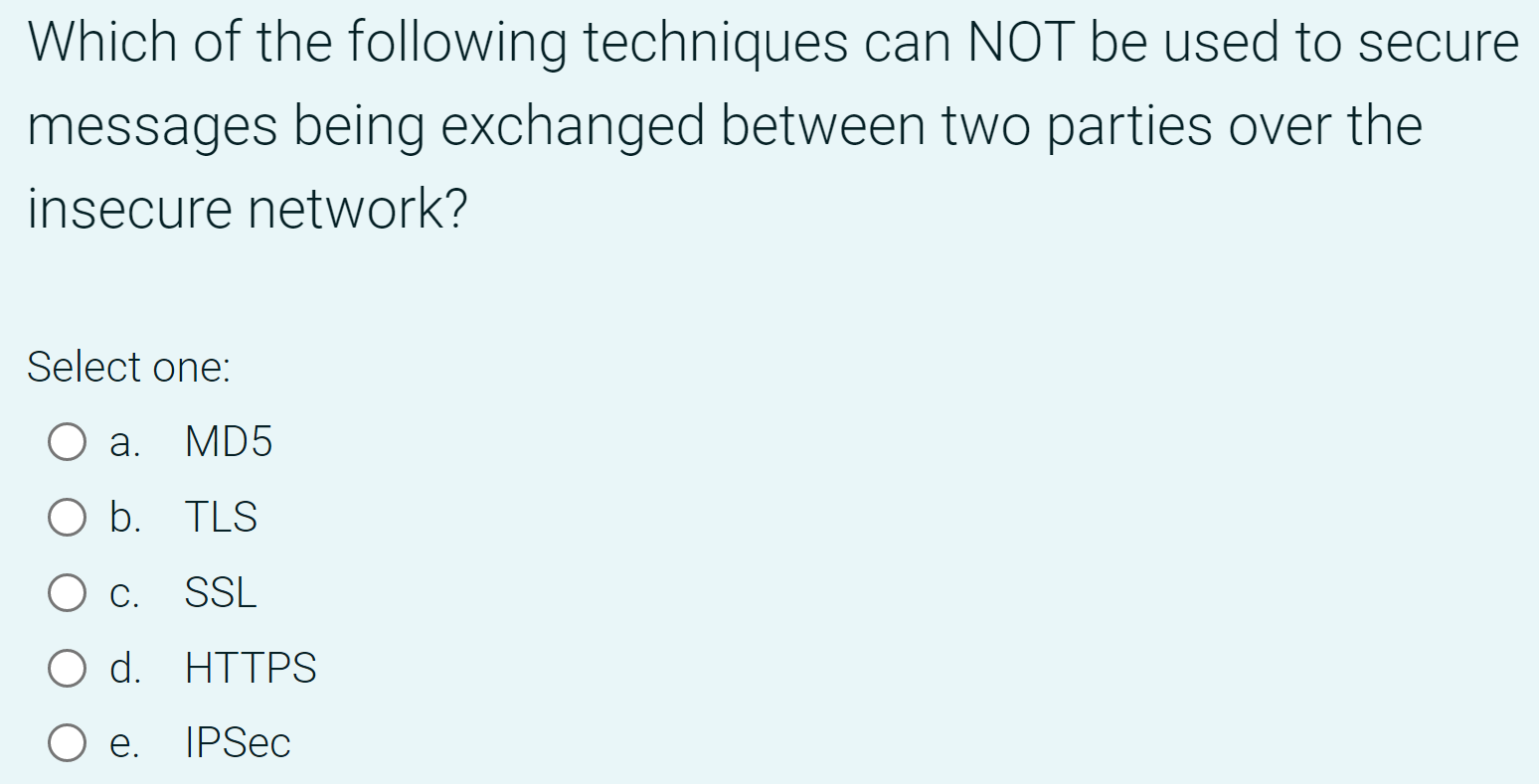 www.chegg.com
www.chegg.com
Solved Internet Protocol Security (IPSec) is A Secure | Chegg.com
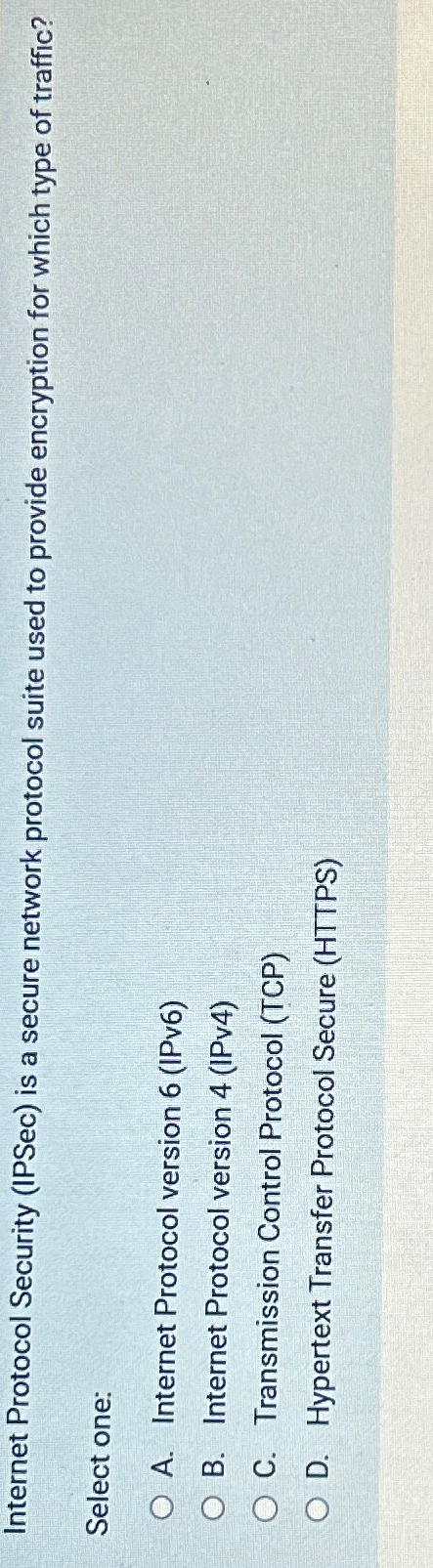 www.chegg.com
www.chegg.com
Understanding Secure Protocols For Data Encryption | Course Hero
 www.coursehero.com
www.coursehero.com
Solved Which Protocol Can Be Used To Secure TCP Connections? | Chegg.com
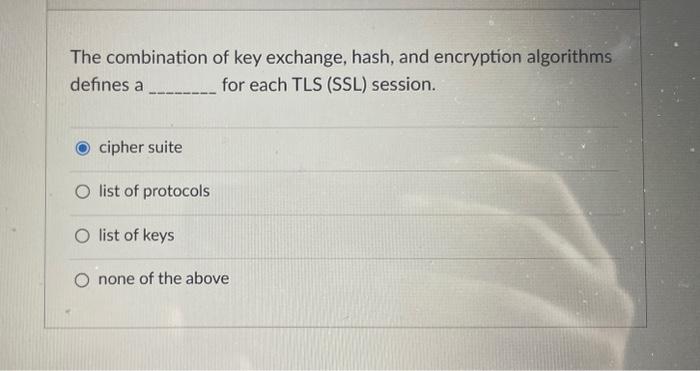 www.chegg.com
www.chegg.com
Solved QUESTION 13 Which Of The Following Is Not A Protocol | Chegg.com
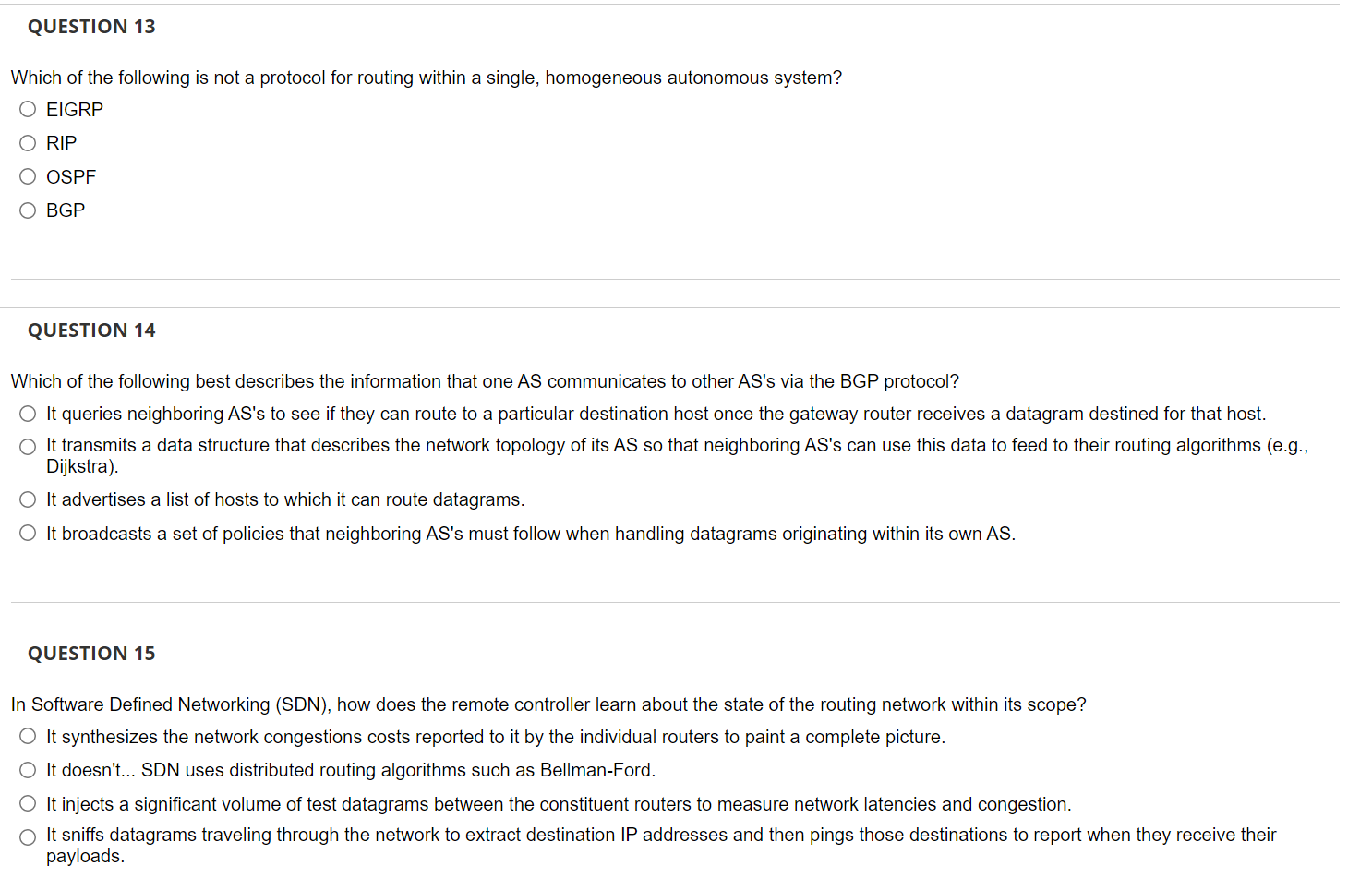 www.chegg.com
www.chegg.com
Solved Which Of The Following Protocols Is Principal | Chegg.com
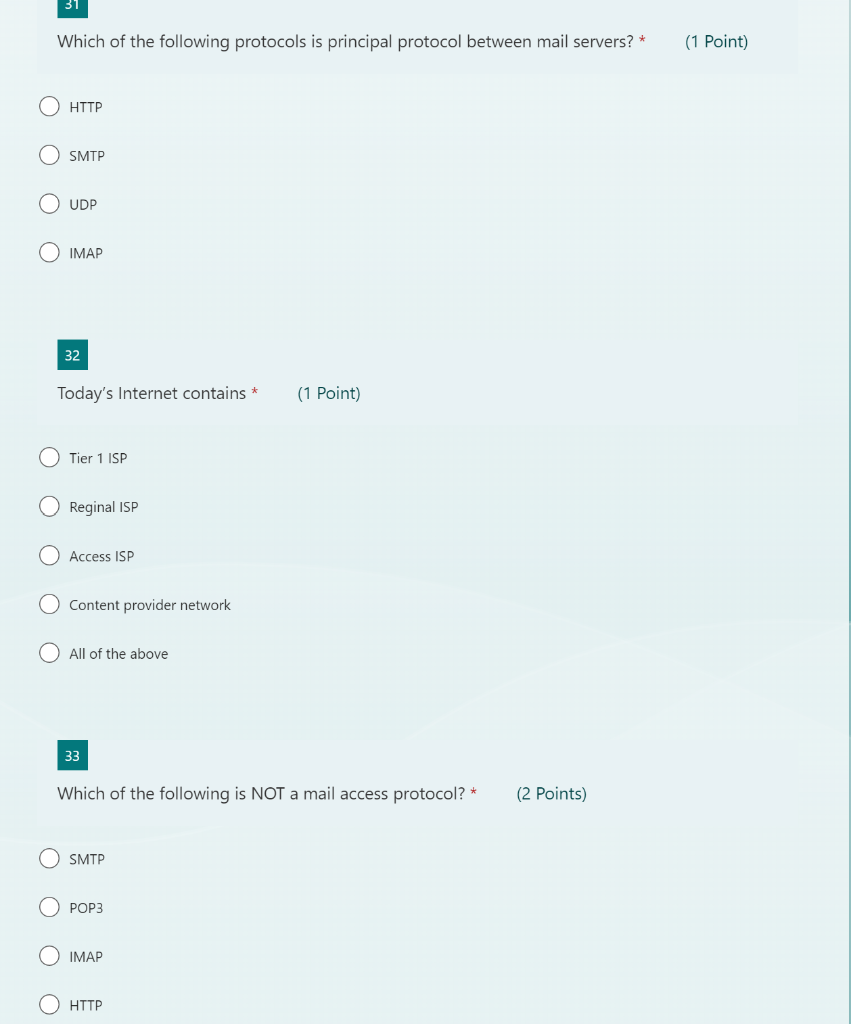 www.chegg.com
www.chegg.com
10.1.2 Secure Protocols 2 - Secure Protocols In This Lesson, We'll Look
 www.studocu.com
www.studocu.com
Solved Question7 of 8Which Of The Following Is A Secure | Chegg.com
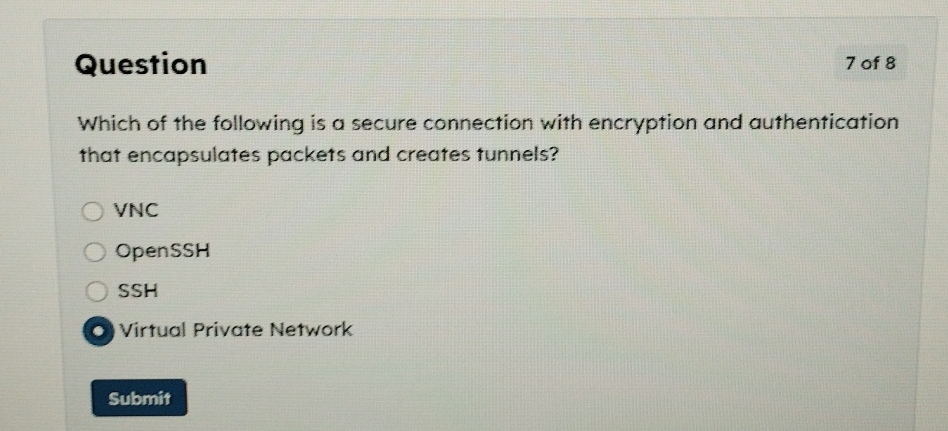 www.chegg.com
www.chegg.com
What Is Secure Socket Tunneling Protocol (SSTP)?
 www.perimeter81.com
www.perimeter81.com
Solved Consider The Following Security Protocol, Established | Chegg.com
 www.chegg.com
www.chegg.com
Solved Question 8 4 Pts The Use Of Cryptographic | Chegg.com
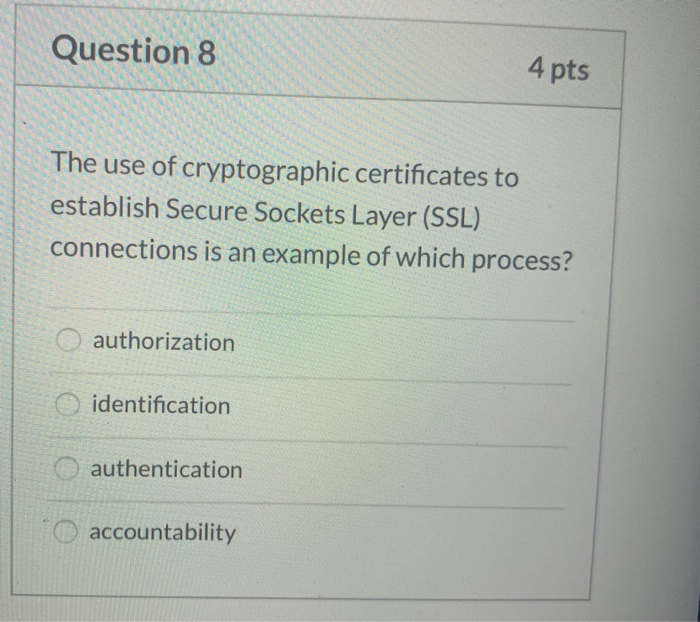 www.chegg.com
www.chegg.com
Solved The SSL Protocol Is Illustrated In The Figure Below. | Chegg.com
 www.chegg.com
www.chegg.com
solved protocol illustrated figure ssl transcribed problem text been show has
Solved Question 21 Of 100 Which Of The Following Types Of | Chegg.com
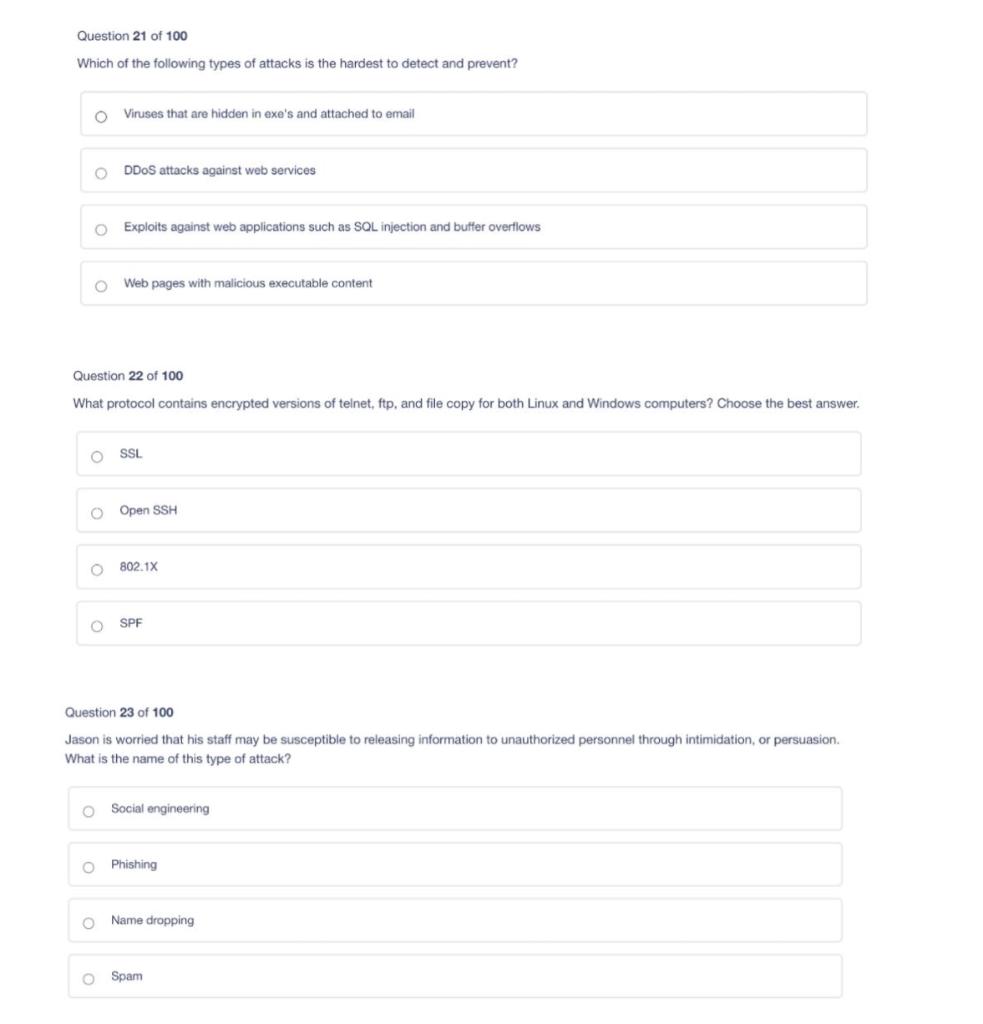 www.chegg.com
www.chegg.com
Solved Which Of The Following Is A Higher-layer Protocol | Chegg.com
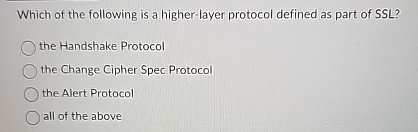 www.chegg.com
www.chegg.com
Security+ Chapter 6: Understanding Secure And Insecure Protocols
 quizlet.com
quizlet.com
Solved Question 3 0.75 Pts Secure Communication Protocols | Chegg.com
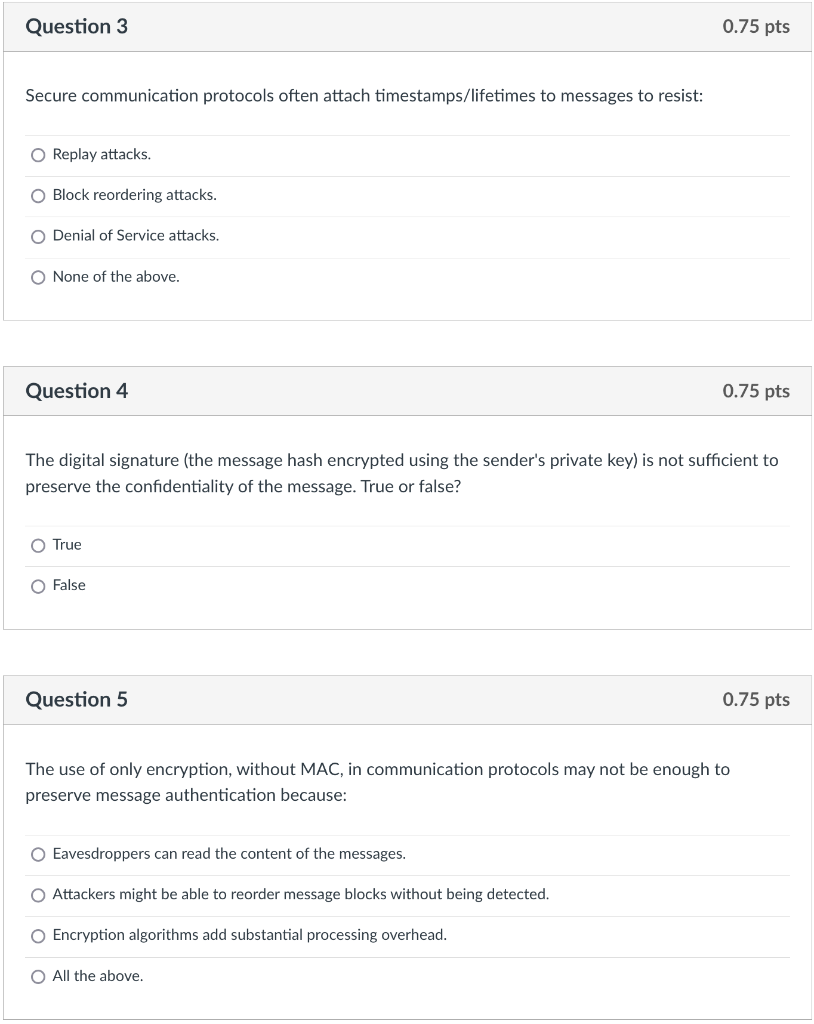 www.chegg.com
www.chegg.com
Solved secure vpns use security protocols and encrypt. Solved which of the following is a higher-layer protocol. Security+ chapter 6: understanding secure and insecure protocols